Disable Azure Security Center recommendations using ARM Templates
Azure Security Center gives you a great overview of the state of your workloads security hygiene and compliance. I recently got tasked with going through the recommendations, take action, and improve our overall security and compliance status. Some of the recommendations presented to me were in the ‘Enable advanced threat protection’-group, like ‘Advanced threat protection should be enabled on Azure App Service plans’.
We had enabled those for our production subscriptions but not for our test subscriptions. The reason for that is simple, it is a pretty expensive feature.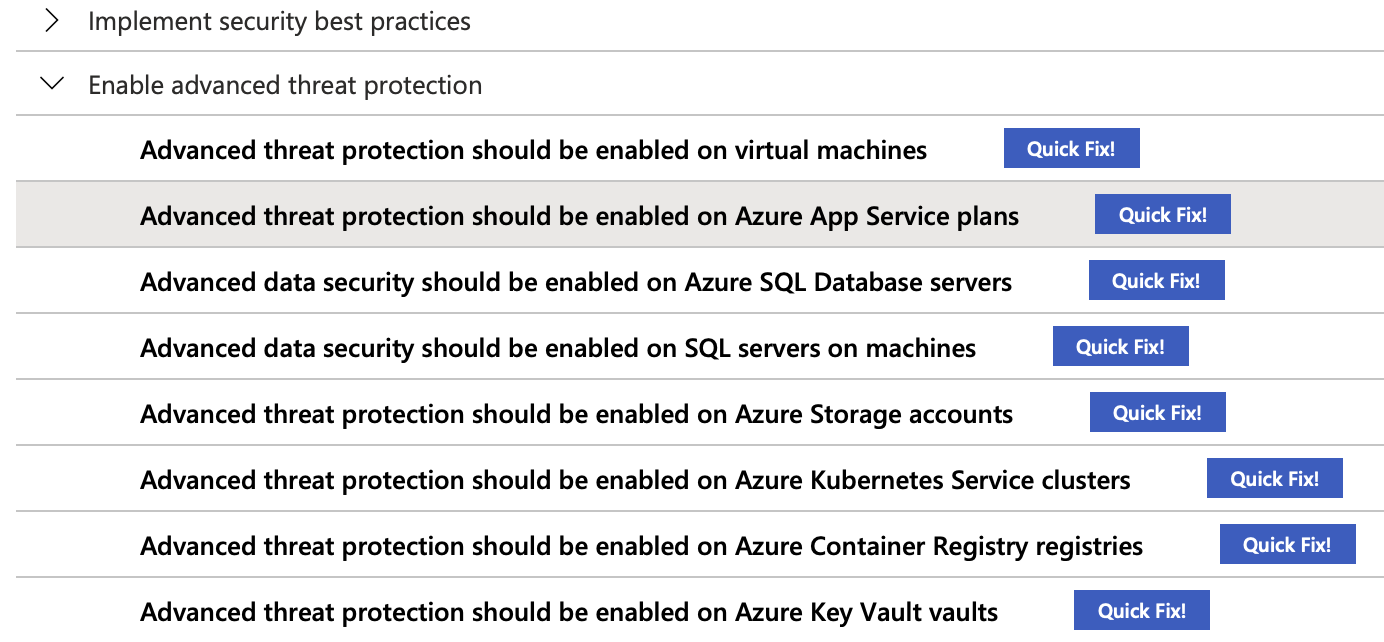 Turning them on means switching your subscription Security Center pricing tier from ‘Free’ to ‘Standard’ because then unlocks ‘Threat protection for supported PaaS services’. That adds 15 dollars to your Azure bill per Azure App Service for example. So, we wanted to stick with the free plan but also disable the recommendation to correct the score. Doing that turned out to be harder than I thought…
Turning them on means switching your subscription Security Center pricing tier from ‘Free’ to ‘Standard’ because then unlocks ‘Threat protection for supported PaaS services’. That adds 15 dollars to your Azure bill per Azure App Service for example. So, we wanted to stick with the free plan but also disable the recommendation to correct the score. Doing that turned out to be harder than I thought…
Azure Policies
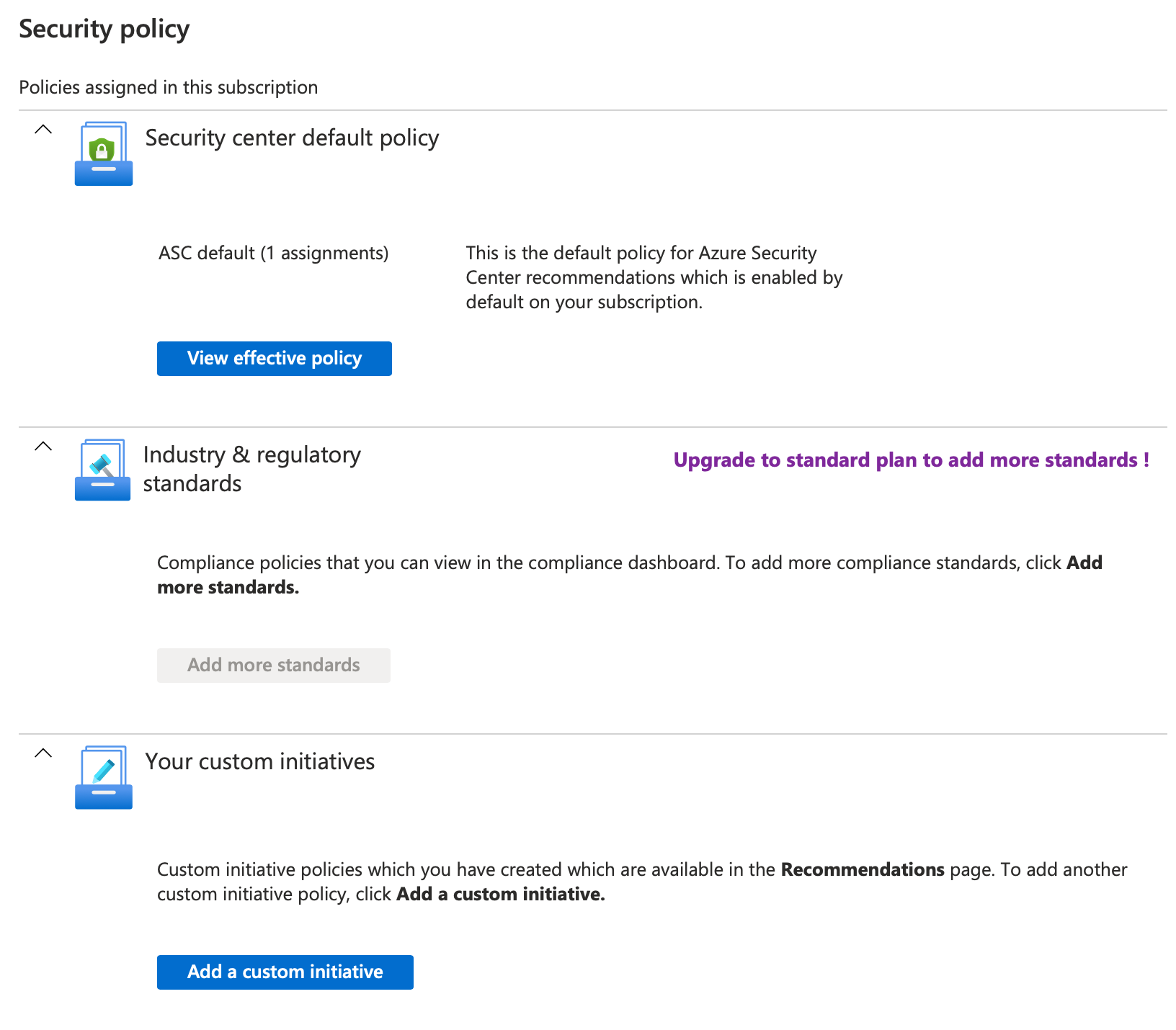
Those recommendations are driven by Azure Policies. If you navigate to Security Center, click Security policy in the menu, select the correct subscription you will be presented with an overview of active policies on that subscription. The ones mentioned above come from the ‘Security center default policy’. Changing them thought the portal is simple and is described here. It does not mention how to do that using ARM templates though.
Disable a policy using ARM templates
The ‘Security center default policy’ is defined by a policy initiative assignment. An initiative is a combination of policies that you can assign as a group. So, to disable the mentioned policies I needed to modify this assignment. That means using a template of type ‘Microsoft.Authorization/policyAssignments’
{
"type": "Microsoft.Authorization/policyAssignments",
"name": "[parameters('policyAssignmentName')]",
"apiVersion": "2019-09-01",
"properties": {
"displayName": "[parameters('policyDisplayName')]",
"scope": "[subscription().id]",
"enforcementMode": "Enabled",
"policyDefinitionId": "[parameters('policyDefinitionId')]",
"parameters": "[parameters('policyParameters')]"
}
}
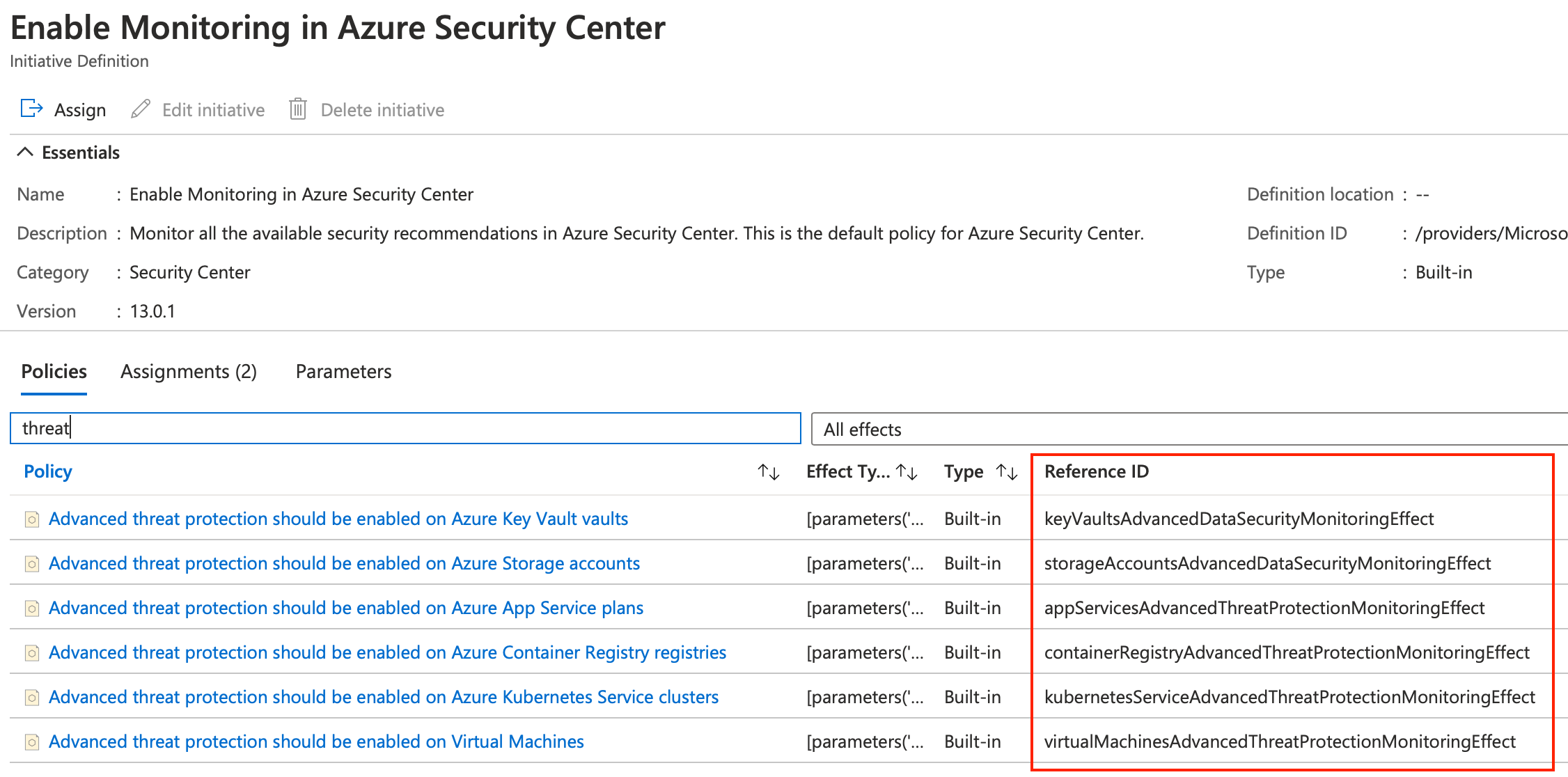
I could not find a Microsoft documentation page on how to get the various specific values I needed so here’s what I did. Go to the security policies and click ‘View effective policy’. Copy the name of the shown assignment, that begins with ‘ASC Default’ followed by your subscription ID. That’s the first piece of information we need as that is your DisplayName. Now go to the All Services -> Policy and find that particular assignment and click it. There you will find the second piece in our puzzle, the actual name: ‘SecurityCenterBuiltIn’. That one is always identical for each subscription I found, it’s just the display name that is different.
Two left, policyDefinitionId and the names of the parameters we want to override. Click on ‘View Definition’. There you can find the definition Id. That one turned out to be identical across subscriptions, not sure about cross tenant. The last piece of the puzzle can be found in the list of policies and specifically in the ‘Reference ID’ column.
 With this information we can build our array of parameters which then looks like:
With this information we can build our array of parameters which then looks like:
"policyParameters": {
"value": {
"appServicesAdvancedThreatProtectionMonitoringEffect": {
"value": "Disabled"
},
"containerRegistryAdvancedThreatProtectionMonitoringEffect": {
"value": "Disabled"
},
"keyVaultsAdvancedDataSecurityMonitoringEffect": {
"value": "Disabled"
},
"sqlServersAdvancedDataSecurityMonitoringEffect": {
"value": "Disabled"
},
"sqlServersVirtualMachinesAdvancedDataSecurityMonitoringEffect": {
"value": "Disabled"
},
"storageAccountsAdvancedDataSecurityMonitoringEffect": {
"value": "Disabled"
},
"kubernetesServiceAdvancedThreatProtectionMonitoringEffect": {
"value": "Disabled"
},
"virtualMachinesAdvancedThreatProtectionMonitoringEffect": {
"value": "Disabled"
}
}
}
The complete resource:
{
"type": "Microsoft.Authorization/policyAssignments",
"name": "SecurityCenterBuiltIn",
"apiVersion": "2019-09-01",
"properties": {
"displayName": "[concat('ASC Default (subscription: ', subscription().subscriptionId, ')')]",
"scope": "[subscription().id]",
"enforcementMode": "Enabled",
"policyDefinitionId": "/providers/Microsoft.Authorization/policySetDefinitions/<policyDefinitionId>",
"parameters": {
"appServicesAdvancedThreatProtectionMonitoringEffect": {
"value": "Disabled"
},
"containerRegistryAdvancedThreatProtectionMonitoringEffect": {
"value": "Disabled"
},
"keyVaultsAdvancedDataSecurityMonitoringEffect": {
"value": "Disabled"
},
"sqlServersAdvancedDataSecurityMonitoringEffect": {
"value": "Disabled"
},
"sqlServersVirtualMachinesAdvancedDataSecurityMonitoringEffect": {
"value": "Disabled"
},
"storageAccountsAdvancedDataSecurityMonitoringEffect": {
"value": "Disabled"
},
"kubernetesServiceAdvancedThreatProtectionMonitoringEffect": {
"value": "Disabled"
},
"virtualMachinesAdvancedThreatProtectionMonitoringEffect": {
"value": "Disabled"
}
}
}
}